PMD is a static source code analyzer. It finds common programming flaws like unused variables, empty catch blocks, unnecessary object creation, and so forth. PMD supports languages such as XML, XSL, Apex, VM, JavaScript, JSP, Salesforce VisualForce, Maven POM, and Modelica. Source code analysis makes any remediation process faster and easier by pinpointing the exact location of vulnerabilities in program code. The detection isolates the bug, and helps you save time and money in fixing any problems.
In this blog, we’ll cover how to integrate PMD for Java, HTML, and PLSQL into your release pipelines in FlexDeploy. After a quick configuration, you’ll be ready to execute PMD scans as part of your pipeline in FlexDeploy.
Configure the PMD Scan in FlexDeploy
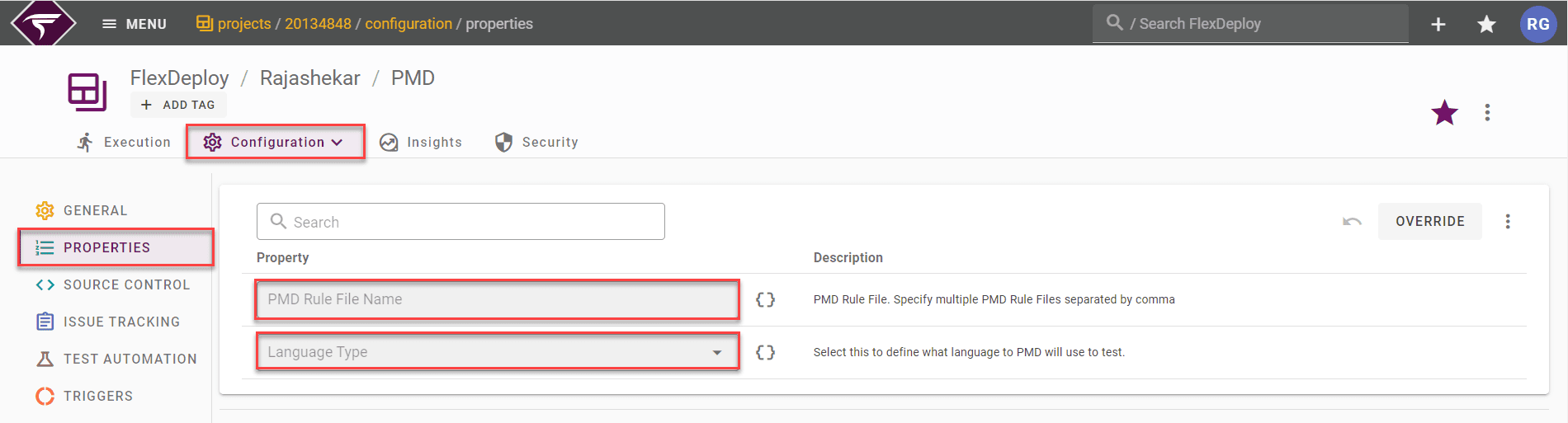
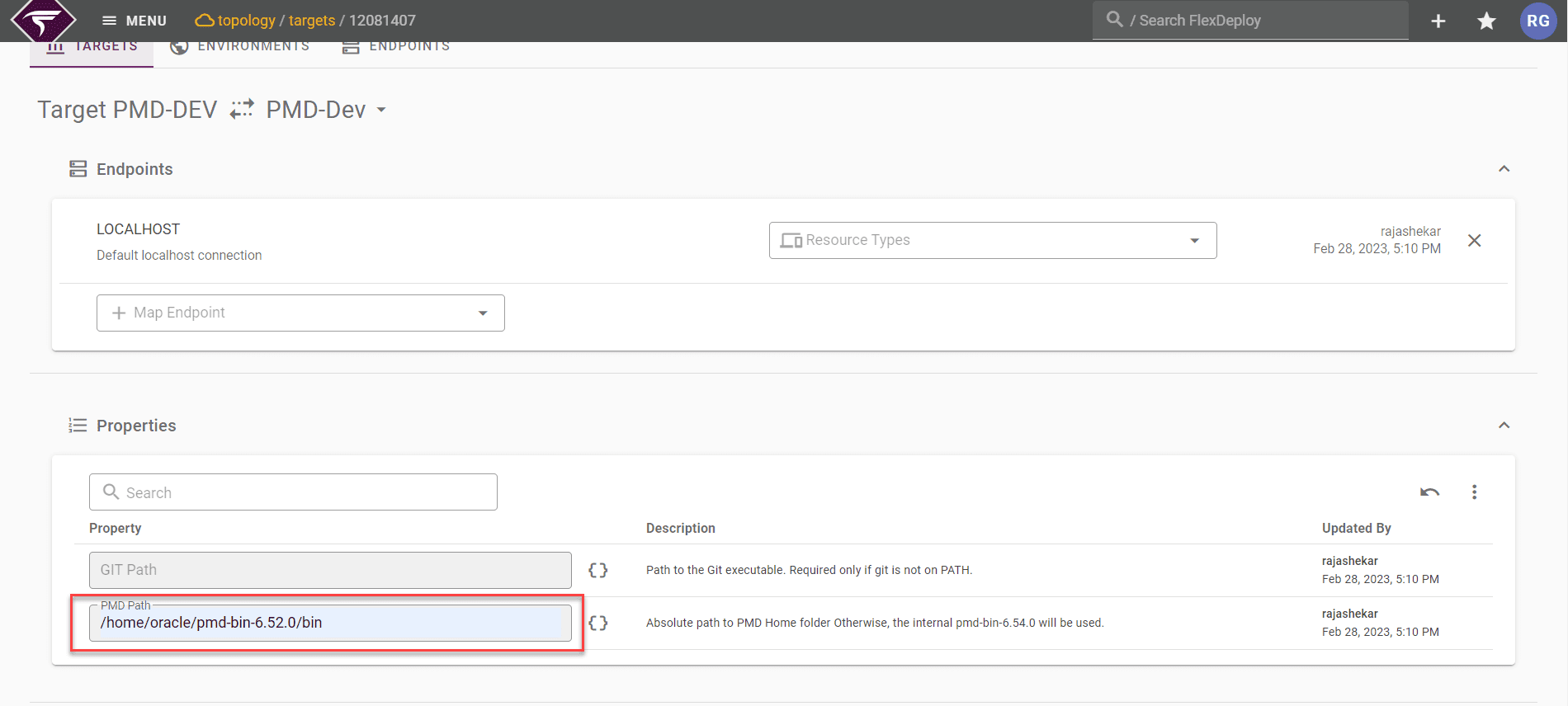
By default, PMD will be installed by FlexDeploy. If you want to work with a different version, Download the PMD installation file. After installation, provide the path in the FlexDeploy configuration screen by going to Topology -> Environments ->Properties. Path configuration is optional if you choose the default PMD version installed by FlexDeploy.
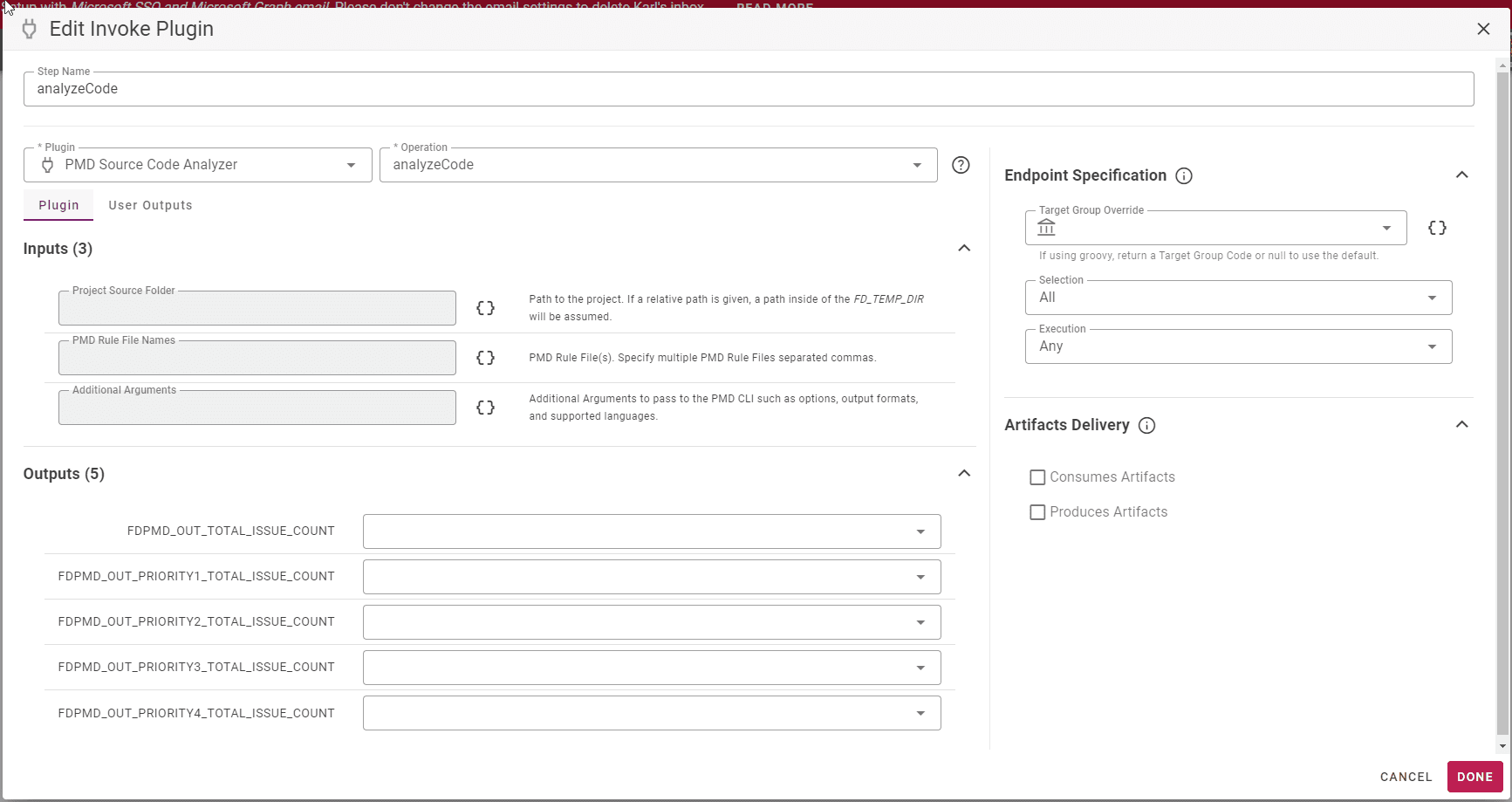
 Add a PMD Scan step to your build Workflow. To include the PMD rules evaluation as part of your build process, open a workflow and include the PMD evaluation as a step.
Add a PMD Scan step to your build Workflow. To include the PMD rules evaluation as part of your build process, open a workflow and include the PMD evaluation as a step.
You can insert the scan before a build if you are sourcing files from SCM.
You have the option to specify a custom rule file(s) on the plugin configuration. This gives you full control over what you want to check and scan in your code. This also eliminates a lot of manual review work. To use a default rule set just select a language on the properties configuration screen.
Execute the PMD Scan
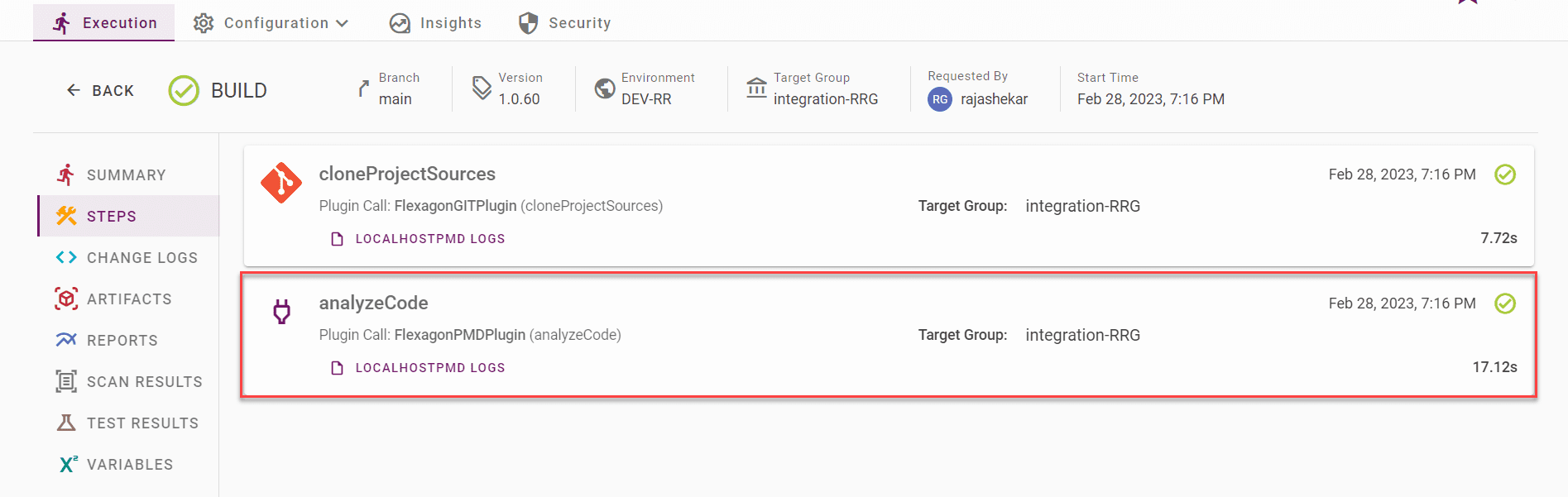
Execute the build manually or using the CI trigger.
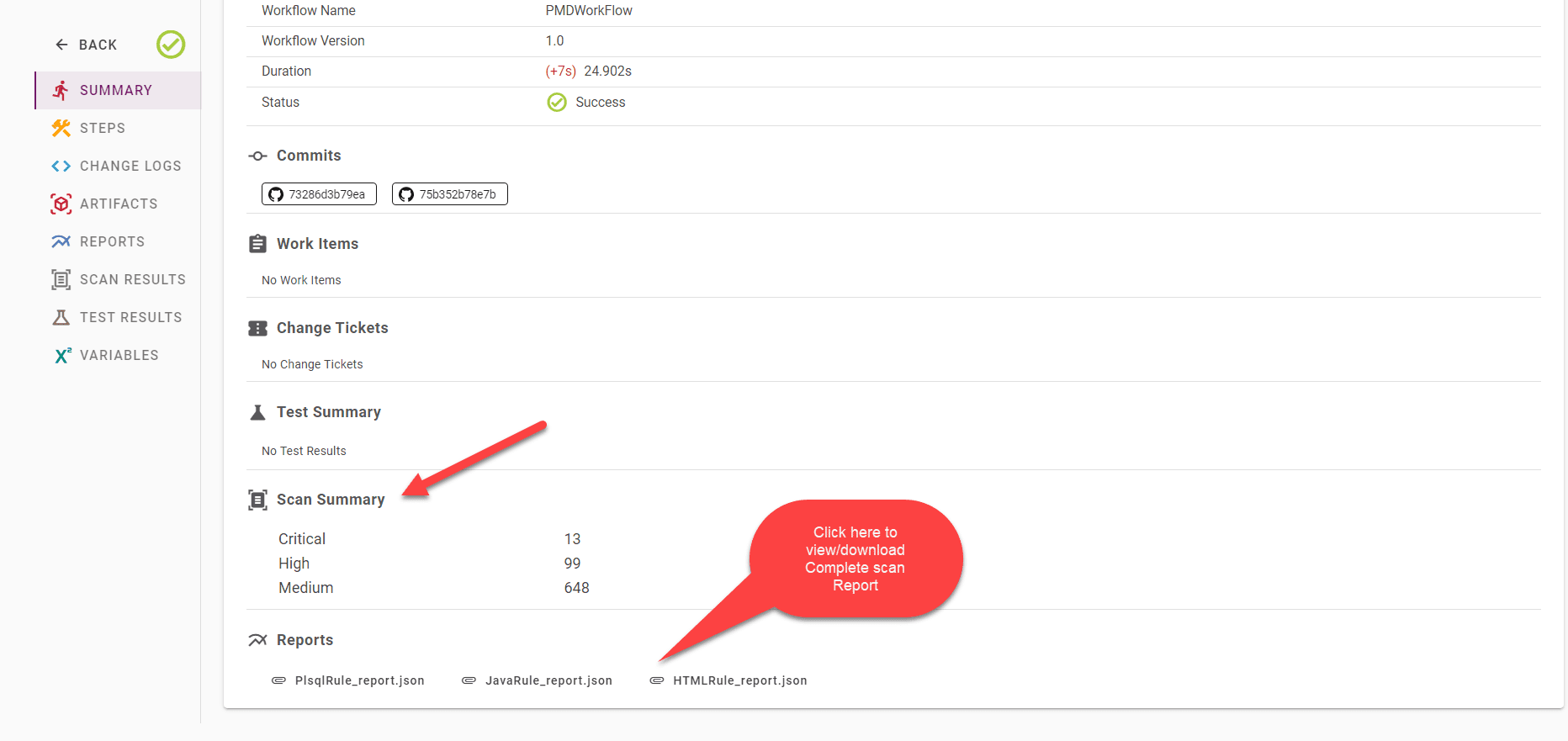
 After the build execution completes, errors or non-compliant code from the to-be-deployed package are captured. Summary counts will be displayed on the summary screen, detailed results will be available on the Scan results tab, and the original report generated by PMD will be available on the reports tab. This report can be sent as an email to the desired audience.
After the build execution completes, errors or non-compliant code from the to-be-deployed package are captured. Summary counts will be displayed on the summary screen, detailed results will be available on the Scan results tab, and the original report generated by PMD will be available on the reports tab. This report can be sent as an email to the desired audience.
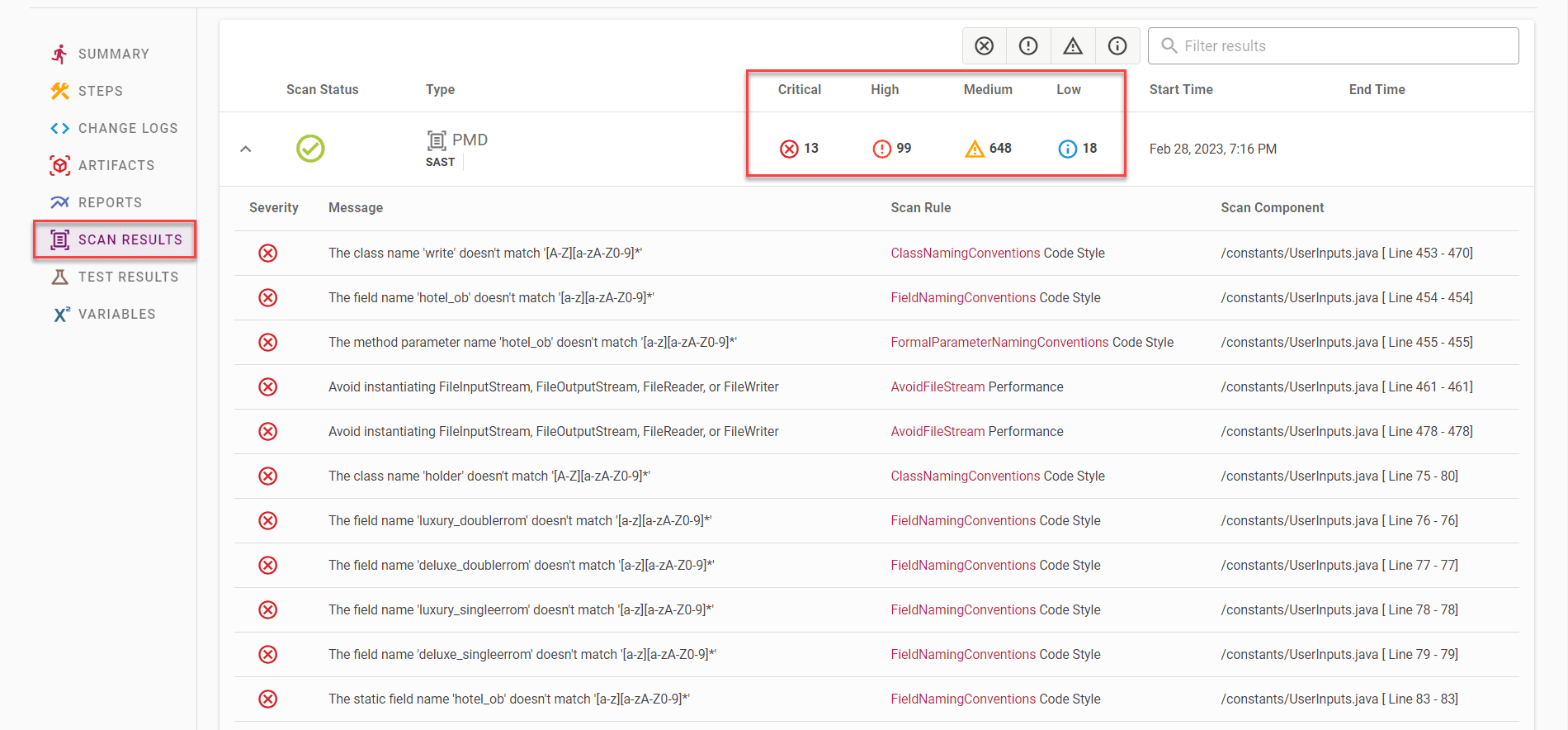
The summary of the scan execution will show the count of Critical, High, and Medium results found.
View the complete information about scan results in the Scan results tab. This report includes information about the severity type, a description of the vulnerability, which scan rule was performed, and in which class with line number the vulnerability was found.
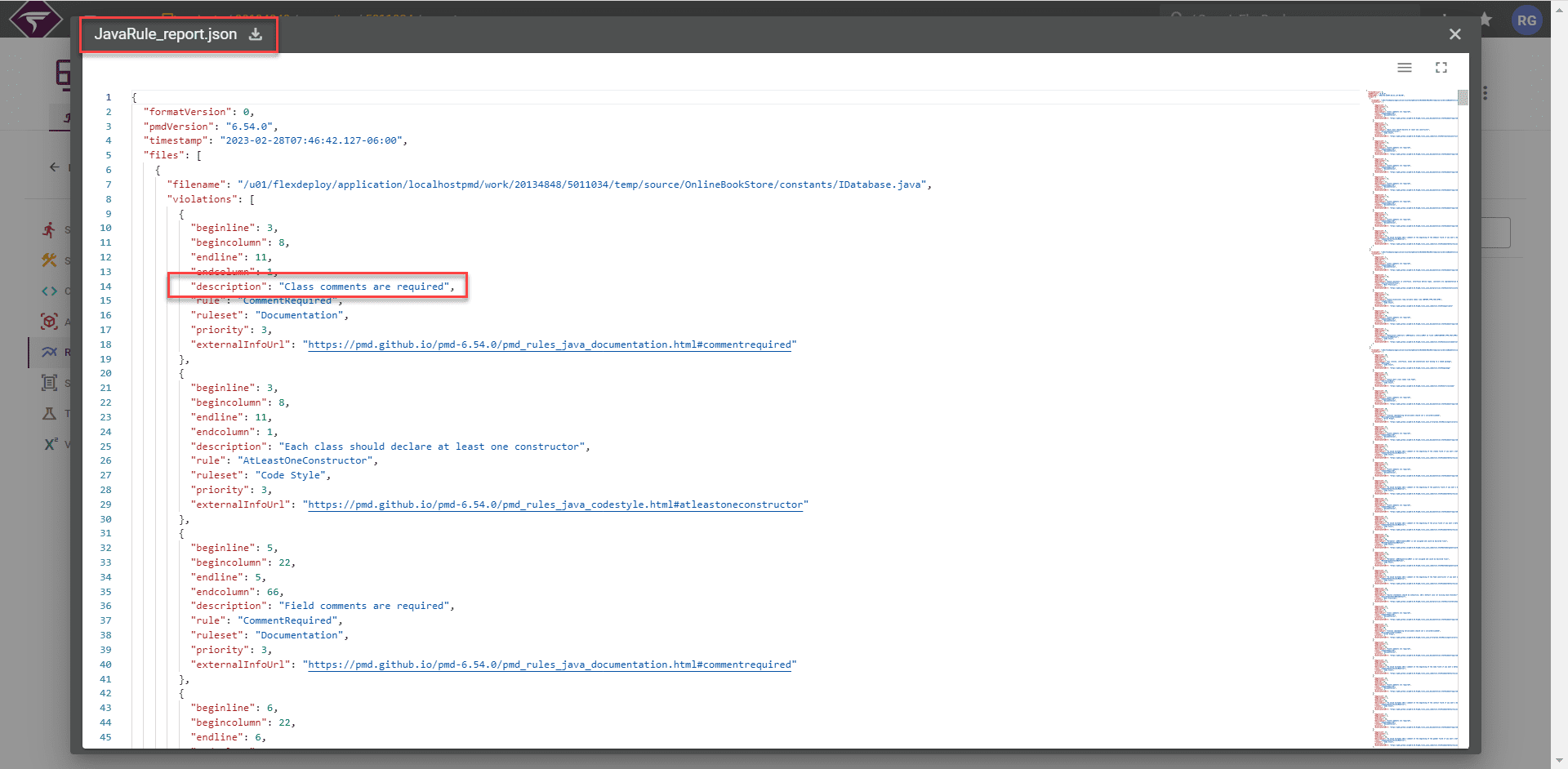
You can view the full original report in the Reports tab. You can also download the report from this tab.
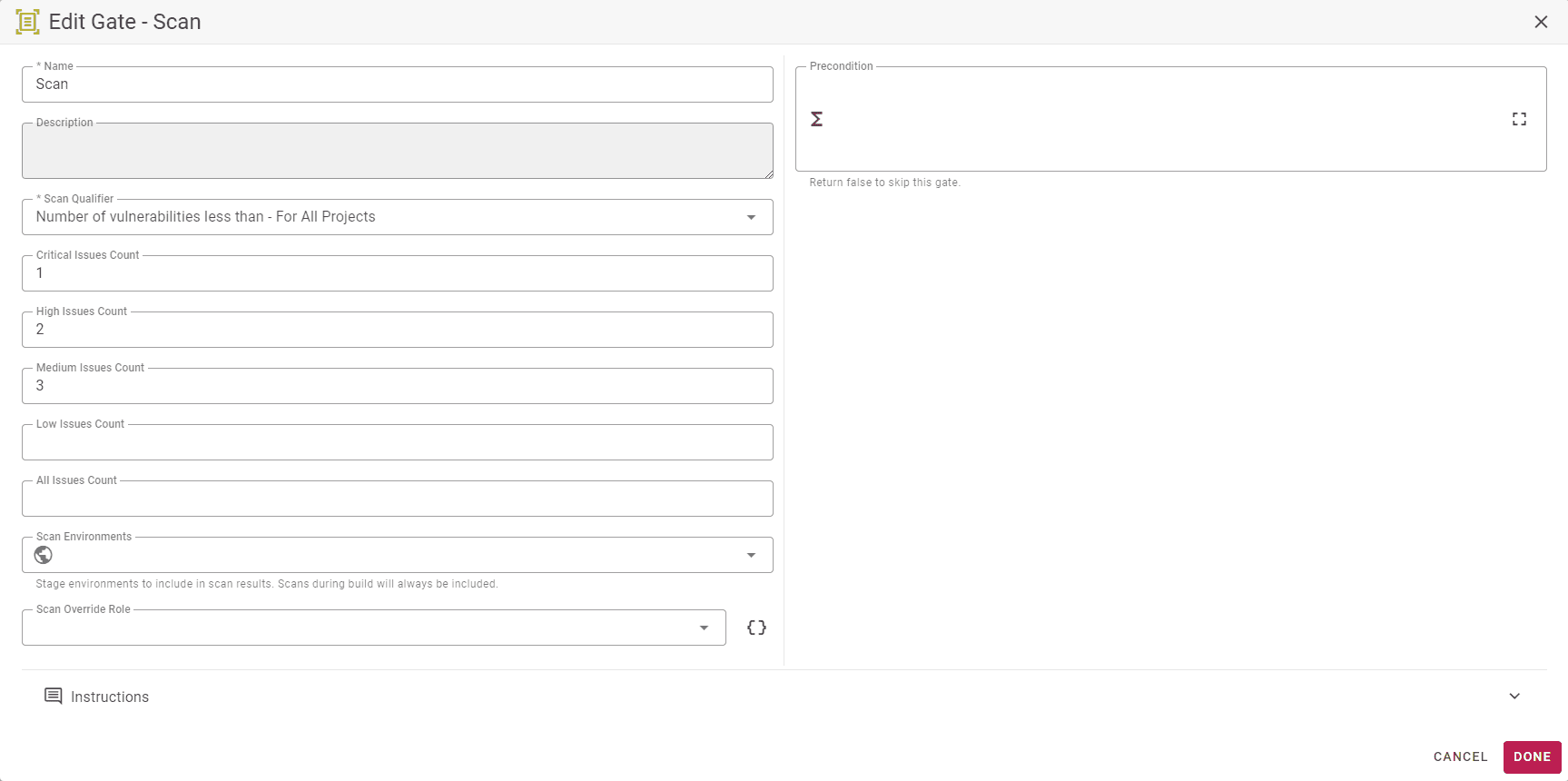
Adding a quality gate in your pipeline will take automated action based on the results of a scan. If needed, set the build to fail when critical issues are found or as per your threshold level.
Conclusion
The PMD source code analysis toolset helps achieve and enforce industry best practices and makes your code more stable and less vulnerable from a security standpoint. You can seamlessly integrate PMD and other scanning tools into your CI/CD pipeline and drive the DevSecOps journey of your organization using FlexDeploy. This will help deliver high-quality code into production fast.