If you’ve been looking for a quick scanner that provides insight into the libraries referenced from your builds, chances are you have seen OWASP dependency-check by Jeremy Long. Dependency Check is a Software Composition Analysis (SCA) tool. SCA is an automated process that identifies open-source software in a codebase, and evaluates the security, license compliance, and code quality. This tool allows a user to run scans on Dependencies, and generates a report for known vulnerable components used in source.
FlexDeploy now has a plugin to integrate with this tool allowing you to gate builds or monitor your servers for vulnerabilities. It also shows the results in project insights so your team has a metric to track progress over time. Let’s look at how the integration works and how you can take advantage of it today.
Gating Builds
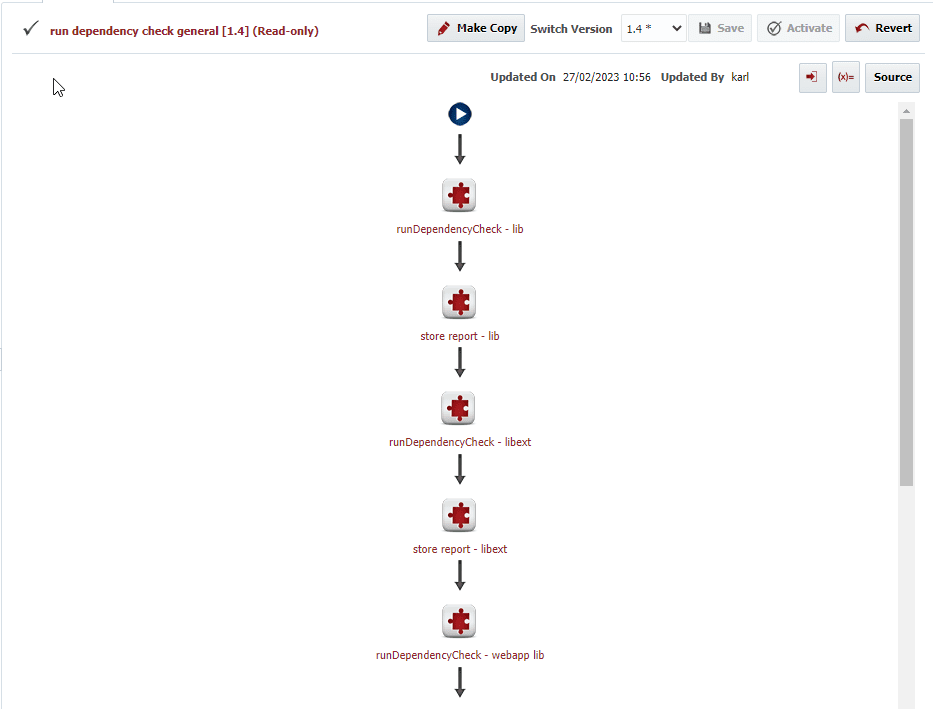
The runDependencyCheck plugin operation can be dragged and dropped into your workflow of choice. This could be a build workflow, allowing you to fail builds that don’t meet your defined criteria.
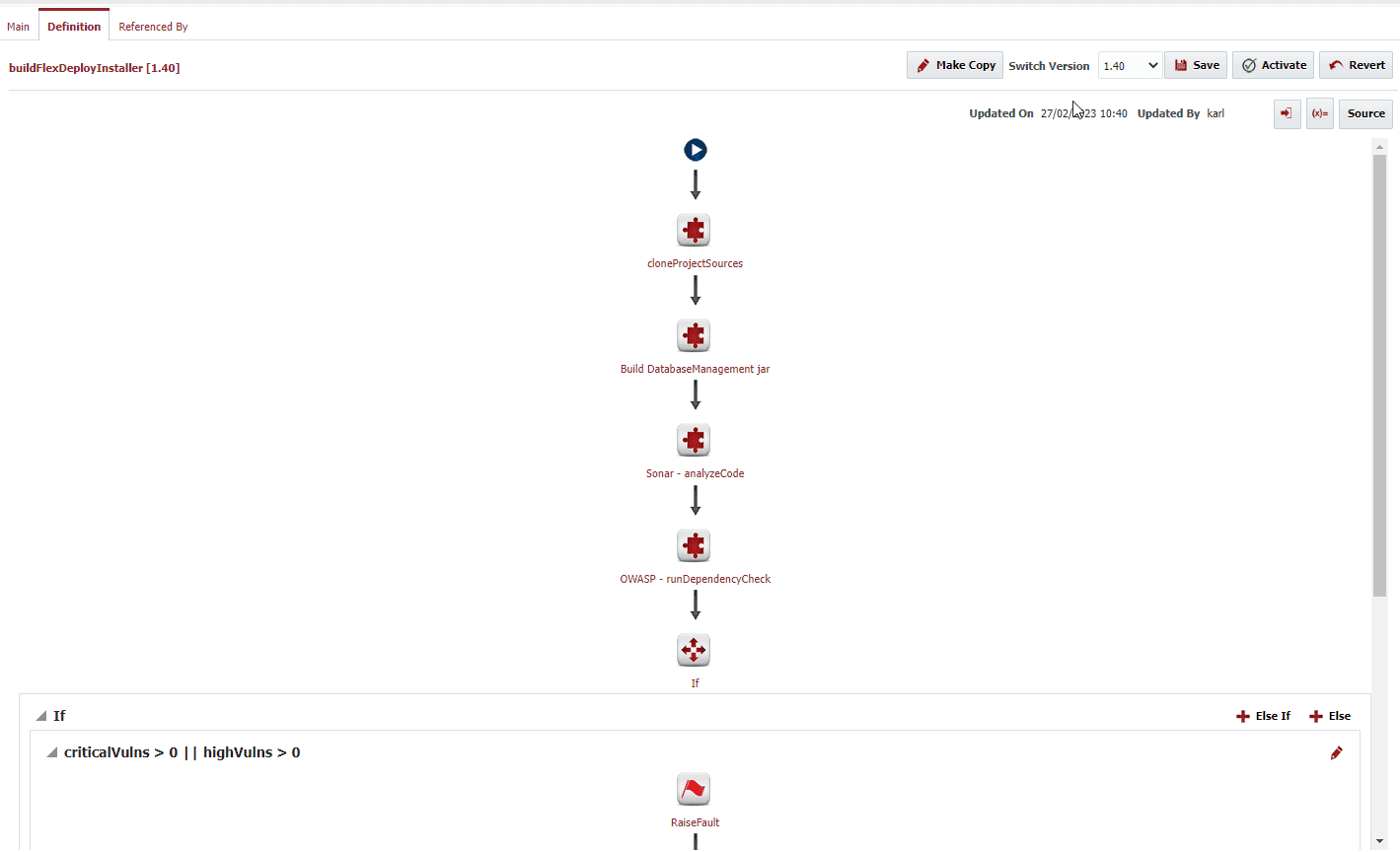
The example shown below is part of the build workflow for the FlexDeploy Installer. The installer build process runs both a Sonar and Dependency-Check scan before the installer is packaged into a final build. The build will never complete if the dependency-check scan fails. That means that if a new vulnerability shows up in one of the libraries that the installer uses to update the database or the drivers that it installs, the build will not complete and our staff will research the new vulnerability and determine the next steps. If it is a false positive, we will suppress this error. If not, we will quickly remediate the vulnerability, ensuring that we don’t ship a version of the installer that contains a vulnerable jar.
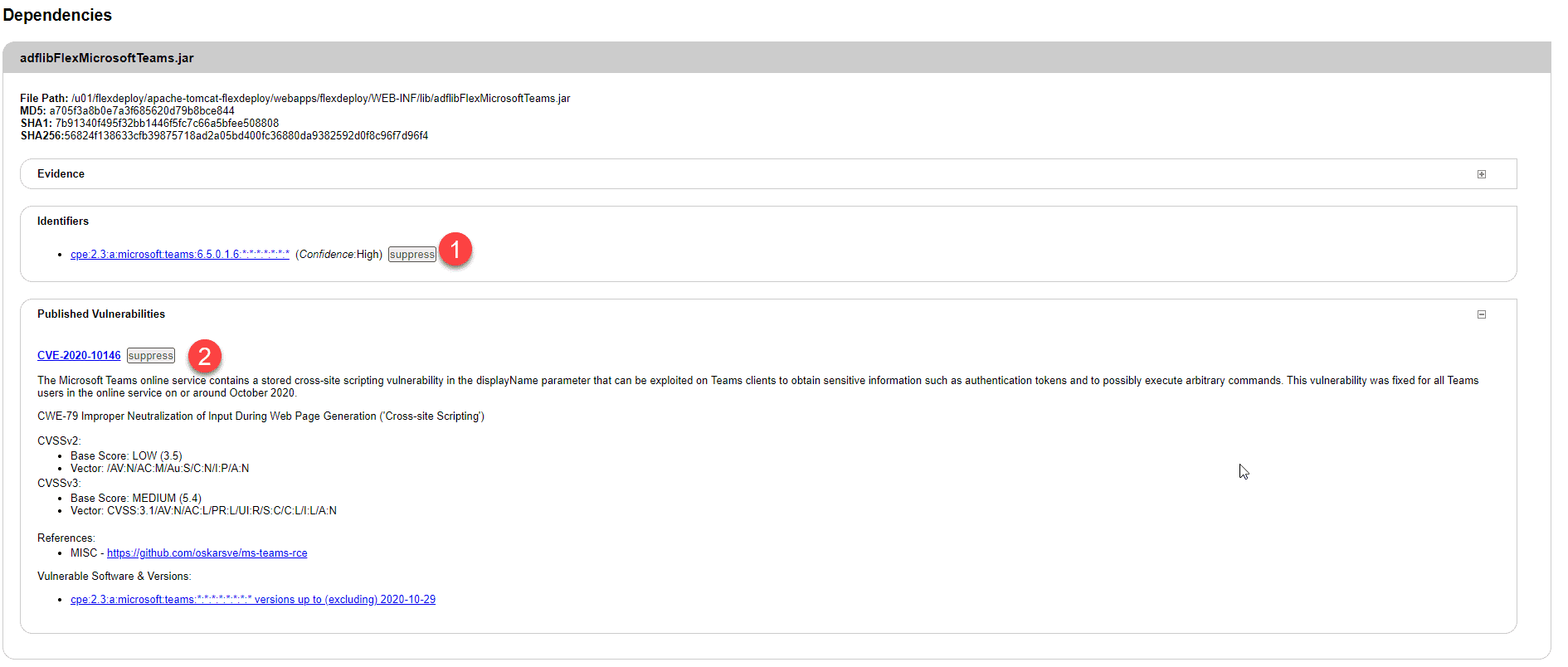
Some of the vulnerabilities that are reported may be false positives. Depending on your libraries and the options you selected, the scanner may think that one of your jars is vulnerable when it is not. You can deal with that by viewing the report that FlexDeploy stores for you and choosing to suppress them. The next screenshot shows an improperly identified library. This library contains our code, but Dependency-Check has identified it as a Microsoft Teams Online library.
In this case, option 1 is what we want and we will suppress the identification of this jar. Option 2 would specify that the vulnerability doesn’t apply.
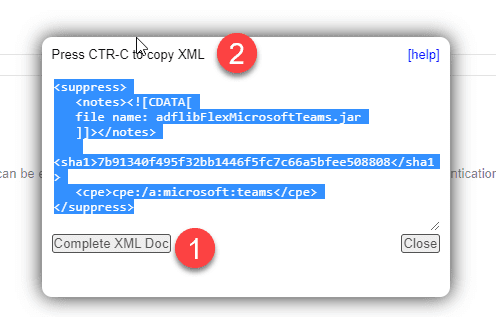
When you click on the button, an xml snippet appears. For the first suppression, choose the complete XML Doc (1). After that, just the snippet is needed (2).
Since this is for a build, the logical place to store the suppress.xml is in source control. In this case, I will store suppress.xml in the project root. FlexDeploy will find it in the FD_TEMP_DIR and use it automatically. If you want to store it elsewhere, you can use the Suppression File Name project property to give FlexDeploy the location.
A vulnerability could also be discovered in the 3rd-party jars your app relies on between build time and the next build or deployment. For this situation, another option might be preferred.
Monitoring 3rd-party Libraries on Your Servers
A utility workflow can be used to scan your deployment targets on a schedule. This helps to track any vulnerabilities that 3rd-party vendors are shipping to you, as well as any vulnerabilities that have come up since the last build or deployment. Here is an example of a FlexDeploy workflow that runs a dependency-check against a development / testing server to verify that no new vulnerabilities have been reported against the 3rd-party libraries that are shipped with the FlexDeploy application.
This workflow runs on a schedule using a project trigger. If the project fails because of new vulnerabilities, the project will send a notification to staff via email. At that point, we will triage the issue to determine what the severity and risk are, if it is a false positive, and which 3rd-party we need to contact.
Flexagon’s Commitment to Quality
Flexagon is working to make sure that we ship safe and reliable code and 3rd-party jars. As an additional step, we notify our customers if there are any issues that are found so that they can learn of the appropriate remediation steps. In 2022, Flexagon provided an improved automated installer to enhance the upgrade process. In 2023, we added an RSS feed so that you can subscribe and track when upgrades are available, the installer is updated, vulnerabilities are found, and more. You can subscribe to this RSS feed using any compatible viewer to get updates.
You can see the key role that FlexDeploy and the OWASP Dependency-Check Plugin play in protecting you from 3rd-party vulnerabilities. In conjunction with other tools, it helps to improve your software quality and security. Flexagon benefits from incorporating the plugin into our internal DevOps process, and now you can enhance your own code development process with FlexDeploy and the OWASP Dependency-Check Plugin.