FlexDeploy is DevOps platform that enables build, deploy and release automation, and provides authenticated integration with Source Code Repository, Issue Tracking & Change Control Systems, Cloud Providers, Applications, Middleware, Databases and more. For example, a token is necessary to work with Jira, or password is necessary to deploy objects to various databases. Given the importance of security in general and the protection of credentials/secrets, credential stores (aka secrets management) like HashiCorp Vault or CyberArk are becoming very popular. Security practice for many organizations dictate change of secrets at regular interval, hence it is important for DevOps platforms like FlexDeploy to integrate with external credential stores.
FlexDeploy integration with external credential stores is focused on retrieval of secure text when necessary, i.e. credentials (password, passphrase, etc.) for connecting to target servers, database, applications, source code repository, issue and change control systems etc. As you would expect, FlexDeploy will not store, cache, print such secrets retrieved from external stores. FlexDeploy also has a local credential store which can be used if a customer hasn’t invested in an external credential store or secrets management product.
High-Level Features
- Out of box integration with
- Easy extension mechanism to integrate with other credential stores
Let’s look at FlexDeploy integration with external credential stores in a bit more detail.
We will walk through in the context of HashiCorp Vault integration, FlexDeploy configuration steps apply equally to other stores.
Credential Store Setup
FlexDeploy uses the recommended method of using AppRole authentication against vault. Here are steps you need to perform on Vault to prepare for integration.
Create specific AppRole for FlexDeploy authentication. Take note of role-id and secret-id. Make sure to assign a policy to FlexDeploy specific AppRole to allow for read access on various secrets paths.
# Reference - https://learn.hashicorp.com/vault/getting-started/apis
# 1. Start by enabling the AppRole authentication.
export VAULT_TOKEN="s.??????????"
curl \
--header "X-Vault-Token: $VAULT_TOKEN" \
--request POST \
--data '{"type": "approle"}' \
http://127.0.0.1:8200/v1/sys/auth/approle
# 2. Create AppRole for FlexDeploy using specific policy
curl \
--header "X-Vault-Token: $VAULT_TOKEN" \
--request POST \
--data '{"policies": ["flexdeploy-policy"]}' \
http://127.0.0.1:8200/v1/auth/approle/role/flexdeploy-role
# 3. Get role-id and secret-id from Vault
curl \
--header "X-Vault-Token: $VAULT_TOKEN" \
http://127.0.0.1:8200/v1/auth/approle/role/flexdeploy-role/role-id
curl \
--header "X-Vault-Token: $VAULT_TOKEN" \
--request POST \
http://127.0.0.1:8200/v1/auth/approle/role/flexdeploy-role/secret-id
4. Create flexdeploy-policy. You will need to create policy hcl file to give flexdeploy-role read access to specific secret paths
./vault policy write flexdeploy-policy flexdeploy-policy.hcl
FlexDeploy Setup
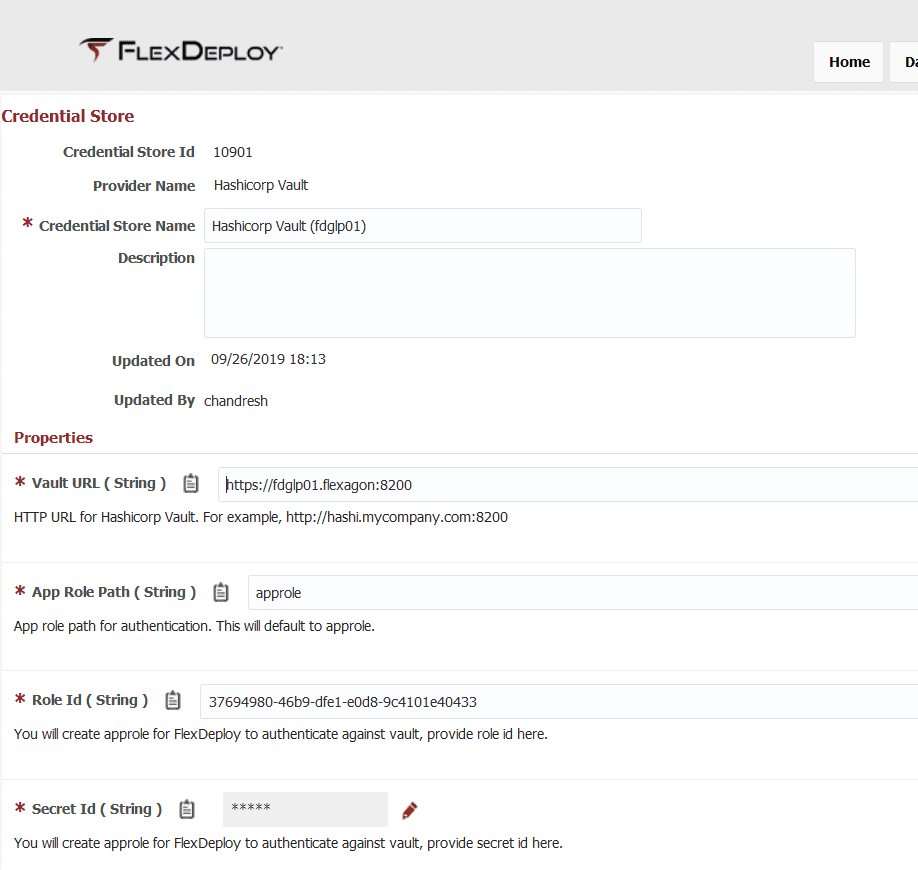
Vault is now ready to accept connection from FlexDeploy, so let’s configure it.
FlexDeploy will communicate with Vault over https using role-id & secret-id to authenticate (we captured role-id and secret-id during previous step). You can also configure the engine version which will default to 2.
This configuration allows FlexDeploy to interact with specific instance of Vault. If you have multiple Vault setup for different purposes, you will create individual configurations in FlexDeploy, i.e. if you want to access secrets from it.
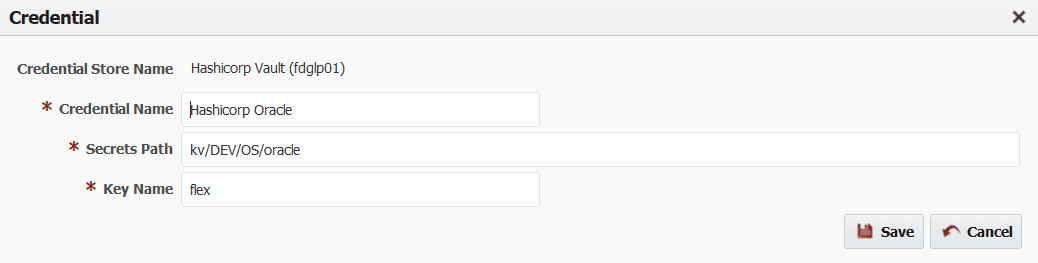
To retrieve a specific secret from Vault, you need Secrets Path and Key Name.
You can give a unique name to each credential configured in FlexDeploy to allow for easier identification. This example credential will retrieve secret from flex Key Name of kv/DEV/OS/oracle Path.
By using FlexDeploy, organizations establish an automated and repeatable process for building, packaging, and safely deploying code, APIs, meta-data changes, and data migrations from development through test to production environments.
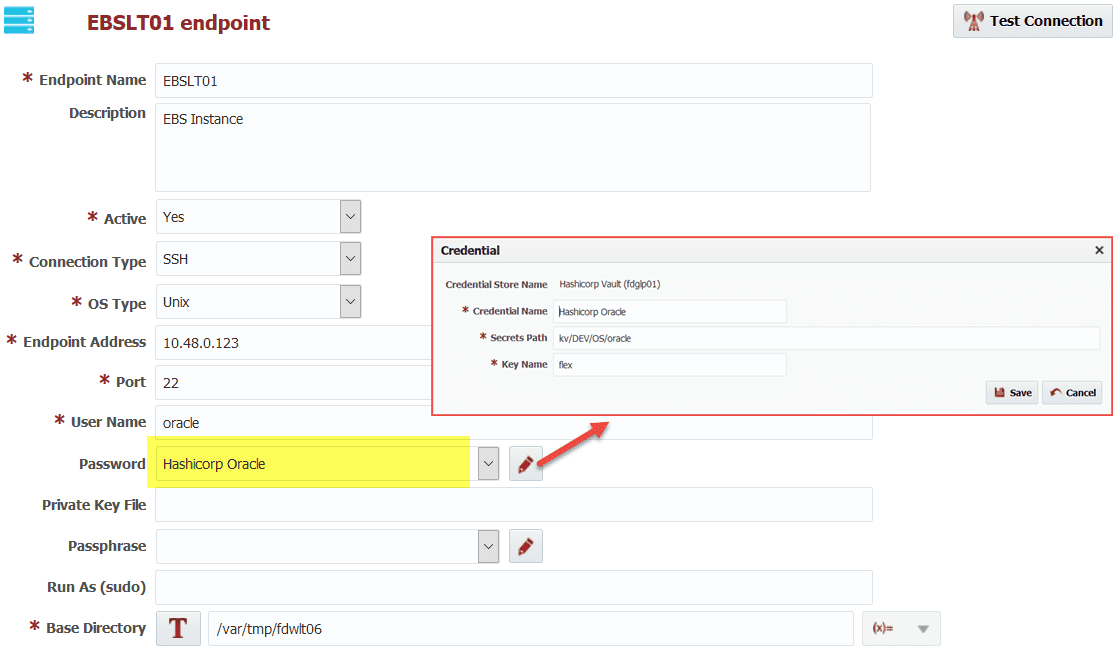
Here is an example use of the credential.
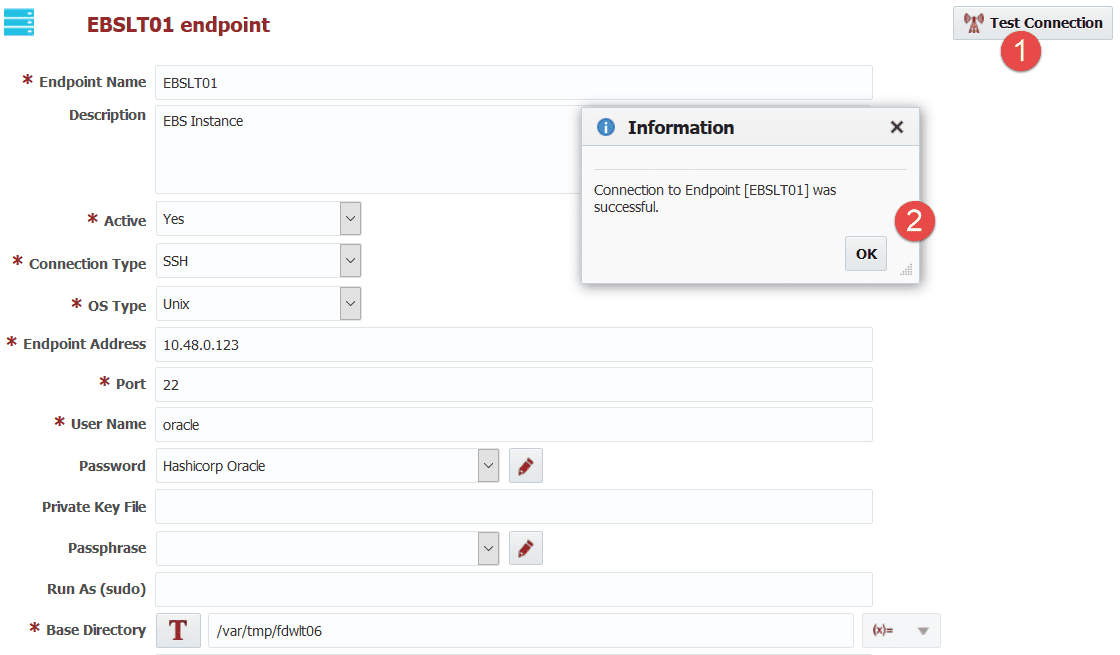
If you click Test Connection on this endpoint, FlexDeploy will connect to Vault using configuration done previously, retrieve secret from secrets path & key name to use it for connectivity check.
FlexDeploy allows you to reuse same credential if necessary. For example, if some development servers use same password for OS user, you can use one credential configuration for all such endpoint configurations.
If you are using CyberArk AAM credential store instead, configuration steps will be similar except you will need to provide CyberArk specific configuration details. Additionally, if you are using a credential store that is not supported out of the box, you can easily perform the integration using Groovy or Java implementation using an API to retrieve credential from store.
You can try FlexDeploy for Free to try features described in this blog.