Security & Compliance
Safeguard Your Application Lifecycle Management Pipeline
Secure. Govern. Comply. Simplify
Empower your organization with a comprehensive approach to security, governance, and compliance. Protect your application delivery pipeline, streamline processes, and ensure regulatory adherence—all while reducing risks and costs.
Proactively address vulnerabilities and prevent unauthorized access.
Implement robust controls for accountability and transparency.
Simplify regulatory adherence with automated auditing and reporting.
Reduce manual tasks with automated approvals and security gates.
Deliver secure, compliant applications that protect your reputation.
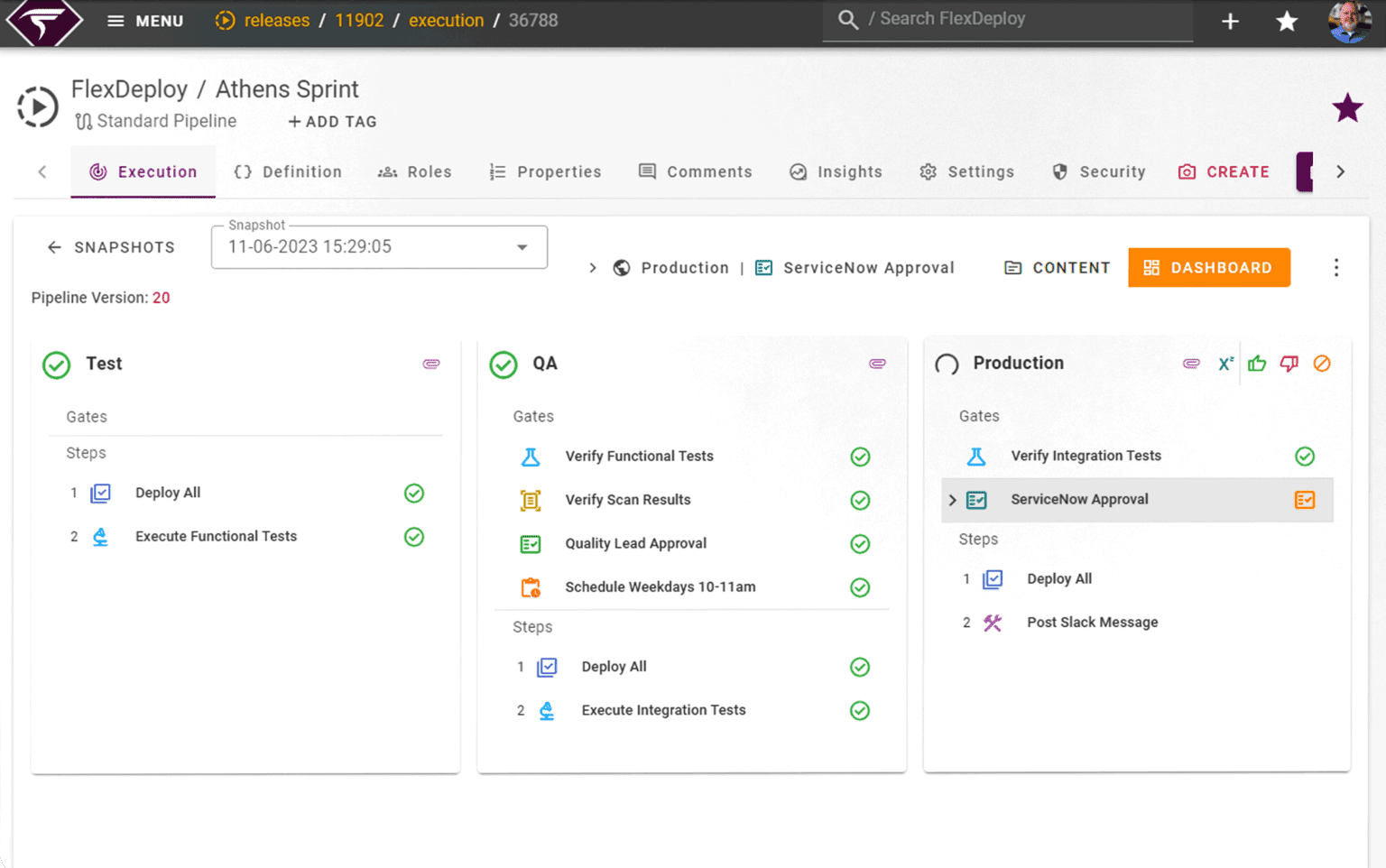
Change management and approval processes
Automate approval gates, track changes with audit trails, and integrate with IT service management to ensure compliance and reduce errors.
- Production change control and scheduling
- Automated approval gates
- Integration with IT service management
- Audit trails and compliance
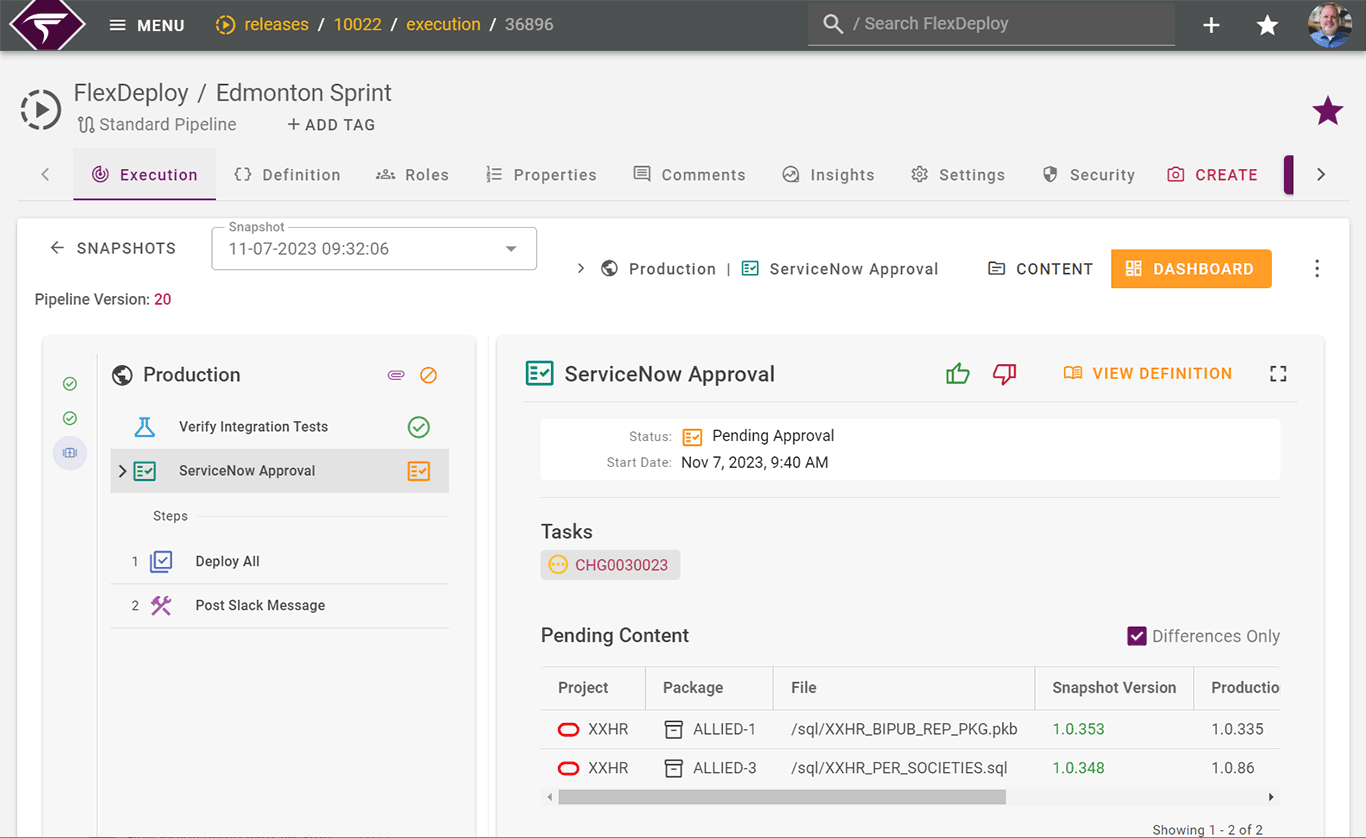
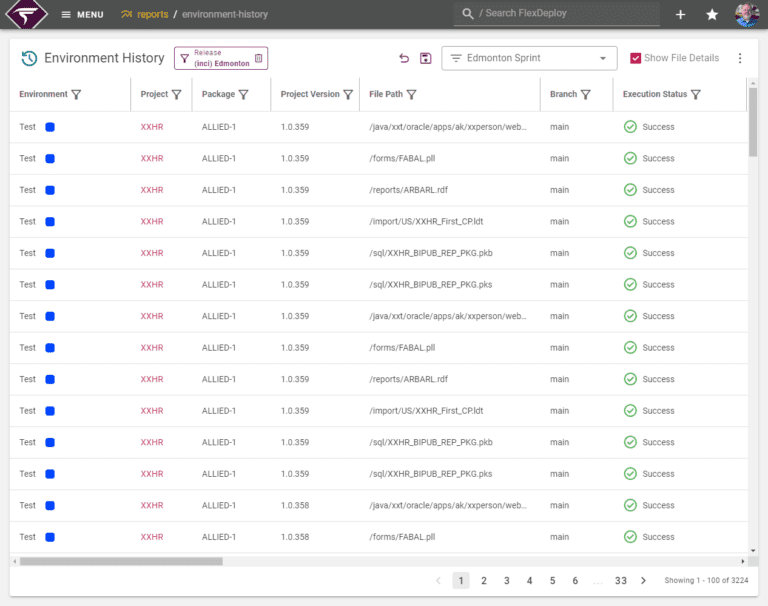
Compliance auditing, reporting and insights
Leverage detailed audit logs, customizable dashboards, and pre-defined reports to streamline regulatory compliance.
- Detailed audit logs
- Pre-defined and built-in reports
- Customizable real-time dashboards
- Project insights for compliance improvement
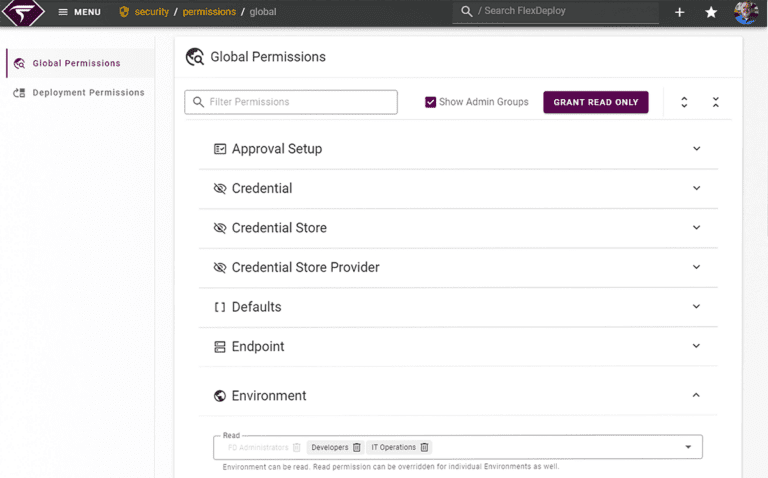
Authorization and role-based access
Implement fine-grained access controls and integrate with LDAP or Active Directory to enhance security and compliance.
- Fine grained RBAC controls
- Authorization framework
- Role-based permissions
- Integration with LDAP or AD
Segregation of Duties (SoD) for Enhanced Security
Divide critical tasks across roles to prevent conflicts of interest, reduce fraud, and ensure robust governance.
Key Benefits of SoD:
- Prevents conflicts of interest
- Creates checks and balances
- Enhances compliance
- Mitigates fraud , errors and unauthorized access
Examples of SoD in Action:
- Enable one user to initiate deployment, and require a second user to approve it
- Separate roles for managing credentials and executing changes
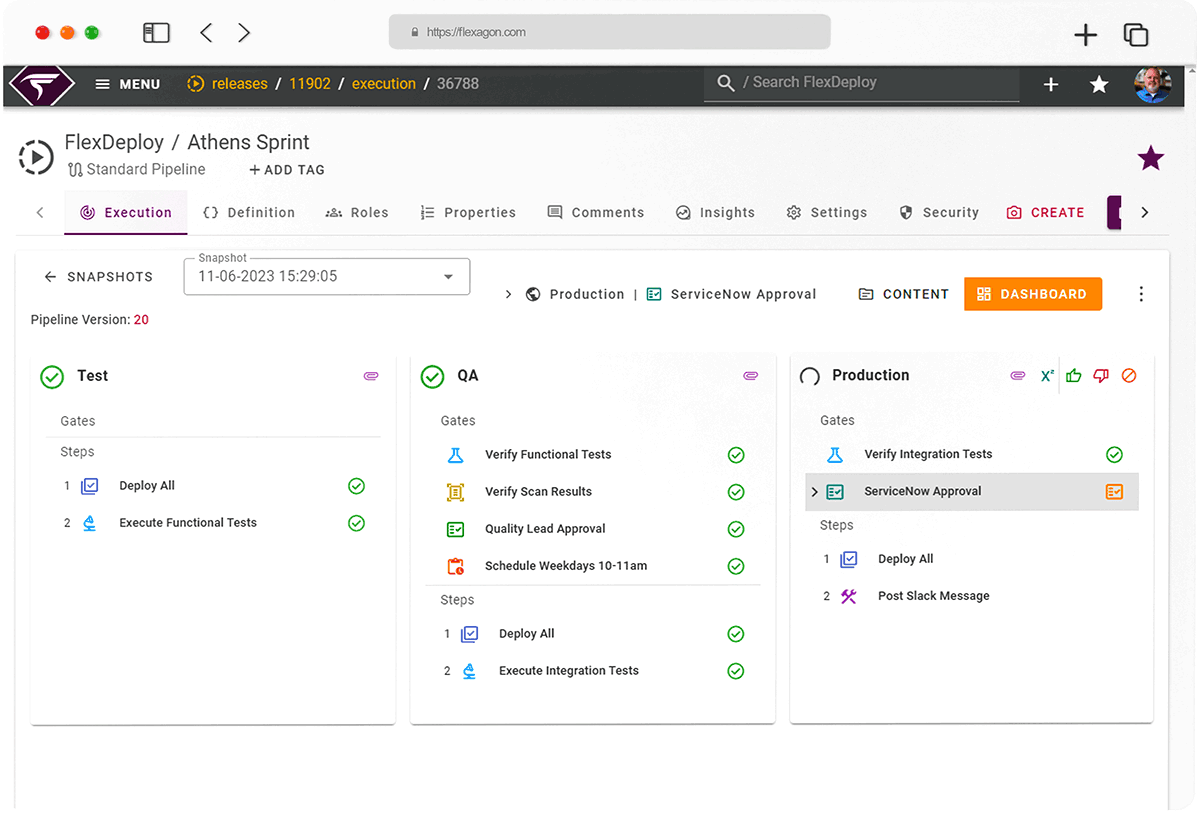
Robust role-based access controls (RBAC) and automated approval gates make it SoD easy to implement and enforce across your software delivery pipeline.
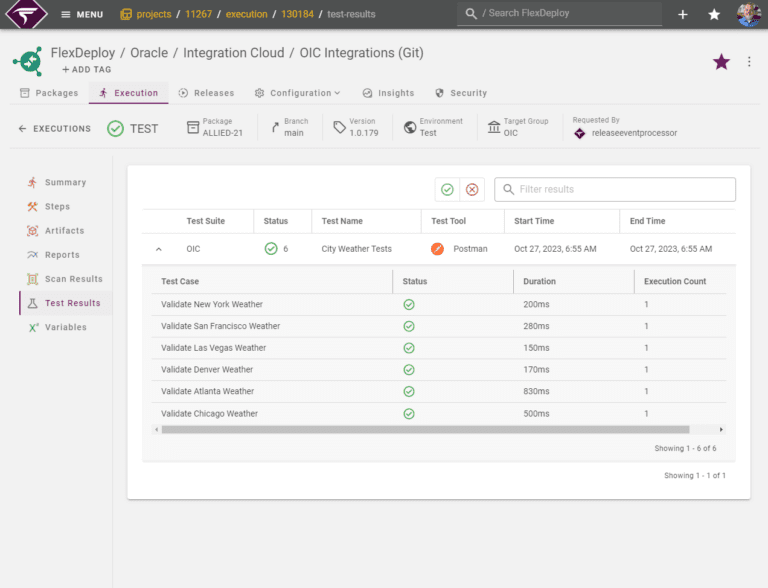
Security and test automation
Integrate streamlined security scanning and testing to identify and mitigate vulnerabilities and quality issues early in your CI/CD process.
- Integrated security testing
- SAST/DAST, and image scanning
- Load testing
- Functional testing
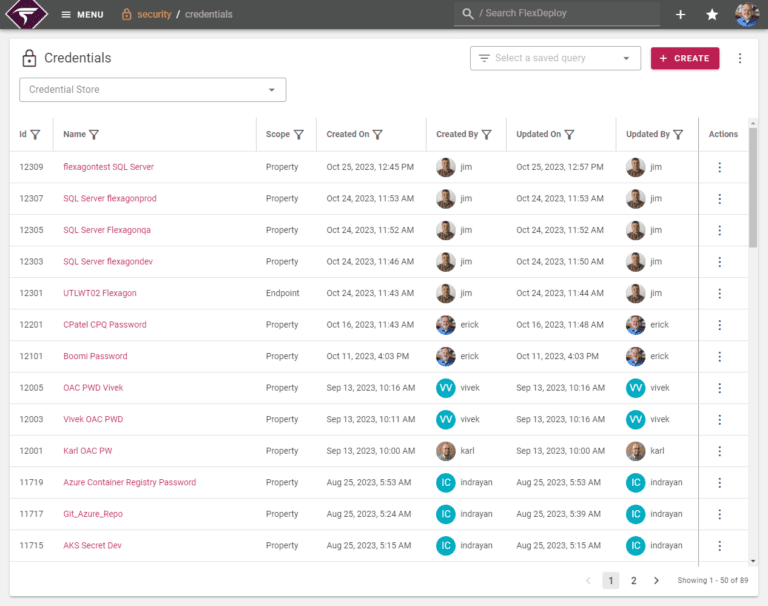
Credentials and secrets management
Secure sensitive data with encrypted storage and managed credentials to prevent unauthorized access.
- Encrypted handling and storage
- Managed credentials and proprietary knowledge
- Secured business-critical and sensative data
Why Segregation of Duties (SoD) Matters
Reduces fraud and errors
Improves accountability and transparency
Simplifies regulatory compliance
Deepen your understanding of security and compliance
Start Here
Familiarize yourself with the security and compliance features that FlexDeploy offers.
-
Set up role-based access controls
-
Leverage built-in credential store or integrate external credential store
-
Implement single sign-on (SSO) and multi-factor authorization (MFA)
-
Define your test strategies and automation
-
Implement security scanning and analysis
- Establish Segregation of Duties (SoD) to divide responsibilities and enhance governance.
Get FlexDeploy Support
Request support or find downloads by logging into the support site. If you are not a current subscriber or are an associate for an existing FlexDeploy customer, please contact us.
Flexagon also provides ongoing Professional Services to support your business system and software goals.
You are also encouraged to find solutions and offer suggestions by participating in the FlexDeploy Users Group.
Review the FlexDeploy Product Roadmap
The FlexDeploy product roadmap is maintained, reviewed, and validated against customer needs. It empowers us to innovate, meet, and exceed customer expectations.
See what’s new in the FlexDeploy Platform.
Search FlexDeploy Documentation
The FlexDeploy User Guide provides comprehensive documentation and information about using FlexDeploy. Users can browse topics, search for specific information, and gain insights into various functions and features.
Curious about what’s new? See the release notes for FlexDeploy 9.0.
Security & Compliance Resources
Articles
Built for the Big Stage: Why Flexagon’s DevOps Is Game-Day Ready
Articles
A Prominent Higher Education & Research Organization Goes Live with FlexDeploy
Case Studies
FlexDeploy and Tririga: Streamlining IT for a Global Fast-Food Leader
Articles
Achieving Robust Governance and Compliance in a Complex Technology Landscape
Manage the entire application lifecycle from a single platform
Flexagon enables organizations to manage both functional and technical application assets from one unified platform. Built on DevOps principles, it brings together configuration management, build and deployment automation, release orchestration, and risk management - providing end-to-end control across the full enterprise application lifecycle